Table of Contents
ToggleWhy Privacy Matters
The Definitive Guide to Protecting Yourself in the Surveillance Age


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 1: Introduction & The Stakes


Your phone buzzes at 2 AM. It is not your alarm. It is a notification from your credit monitoring app. Someone in another state just tried to open a line of credit in your name. You have never been to that state. You do not know how they got your Social Security number, your mother's maiden name, or the answer to your security question about your first pet. But they did. And now you are awake in the dark, wondering how deep this goes.
Three Stories That Actually Happened
I will start with three people. Their experiences are documented, verified, and in some cases, still ongoing. I tell you about them not to scare you, though they might. I tell you about them because privacy violations are not abstract. They land on specific humans at specific times. They carry weight that annual data breach statistics can never quite capture.
Rebecca's Year of Living Dangerously


Rebecca Heilweil was 25 in 2021 when she downloaded a period-tracking app called Flo. Millions of women used it. The interface was clean, the predictions were helpful, and the company promised discretion. What Flo did not advertise was that they were sharing users' intimate health data with Facebook and Google. Not in some vague, aggregated way. Specific details about pregnancy attempts, miscarriages, menstrual cycles flowing to data brokers who could connect those dots to Rebecca's identity across the web.
When the Federal Trade Commission investigation became public in 2021, Rebecca learned that her most private biological information had been treated as marketing fuel. She deleted the app, but the data was already out there. Copies exist in servers she will never access, profiles built from her body that she cannot erase. "I felt like my own biology had been weaponized against me," she told Consumer Reports. The FTC fined Flo $200,000. Rebecca got no compensation, no notification of exactly what was shared, and no way to claw it back.
Matthew's Face Becomes Someone Else's Crime


Matthew Banta lived in Wisconsin in 2019. He was 30, worked in IT, and had a clean record. Then police showed up at his door with a warrant for his arrest. A facial recognition system had flagged him as a suspect in a theft at a local store. The match came from a grainy security camera photo. The algorithm said Matthew and the thief shared a 98% similarity score.
Matthew spent three days in jail before investigators realized the obvious. He had been at work, 40 miles away, when the theft occurred. His employer confirmed it. Security footage from his office confirmed it. The facial recognition system had been wrong, but the burden of proof fell on Matthew to demonstrate his innocence. The 98% match that police treated as near-certainty meant nothing in reality. He lost his job while detained. His mugshot appeared in local news before anyone verified the story. Two years later, he was still fighting to get the arrest expunged from his record.
"I used to think, if you have nothing to hide, you have nothing to fear. I was wrong."
-- Matthew Banta, speaking to the Milwaukee Journal Sentinel
Ahmed's Family Dinner Becomes Evidence
Ahmed Al-Rumaihi was a U.S. citizen living in Texas in 2022. His elderly parents had immigrated from Yemen decades earlier. Every Sunday, the extended family gathered for dinner. They spoke Arabic. They discussed politics, the news from home, their worries about relatives still in Yemen. These were ordinary conversations in millions of immigrant households across America.
Then Ahmed applied for a government security clearance for his new job. The investigation turned up something he never anticipated. Immigration and Customs Enforcement had been collecting location data from his family's phones through a data broker called Venntel. The family's Sunday dinner location, a restaurant in Houston, appeared in government databases alongside Arabic-language keywords flagged by automated systems. Ahmed was not the target. But his location data, purchased from a broker that bought it from an app he had installed years ago, became part of a profile. His clearance was denied. The official reason cited "potential foreign influence concerns."
Ahmed had committed no crime. His family had committed no crime. They had simply existed, in a specific place, speaking a specific language, while carrying phones that treated their location as a product to sell. The data broker contracts were legal. The government purchase was legal. Ahmed's ruined career prospects were simply collateral damage in a surveillance economy he never agreed to join.
The "Nothing to Hide" Fallacy and Why It Breaks


I have heard the argument dozens of times. Usually delivered with a shrug. "I have nothing to hide, so why should I care about privacy?" It sounds reasonable. It feels like common sense. It is also completely wrong, and the stories above show exactly why.
The fallacy assumes that privacy is about secrets. That privacy violations only matter if you are doing something shameful or illegal. This misses the entire point. Privacy is not about hiding wrongdoing. Privacy is about context, control, and the right to decide who knows what about you.
Let me offer a concrete example most people can feel in their gut. You close the bathroom door when you use it. Not because you are doing something wrong. Not because you are ashamed of normal bodily functions. You close the door because privacy serves a function even for completely innocent activities. It creates space. It maintains dignity. It allows you to exist without an audience.
Your digital life works the same way. You do not want your employer knowing your medical history because it is irrelevant to your job performance and could bias their decisions. You do not want advertisers knowing your grief after a miscarriage so they can serve you baby product ads. You do not want insurance companies calculating your premiums based on location data that shows you visit fast food restaurants weekly.
None of these scenarios require you to be "hiding" anything. They simply require other parties to lack information that they could use against you. Information asymmetry is power. When Facebook knows everything about you and you know nothing about how they use it, you are not in a fair relationship. You are in a surveillance relationship.
Here is another angle. The definition of "wrongdoing" changes. Marijuana possession was criminal in most states ten years ago. Today it is legal in many. LGBTQ relationships were criminal in living memory. Interracial marriage was illegal within my parents' lifetime. If you believe you have nothing to hide, you are betting that every law, every social norm, every employer's values will remain static forever. History suggests otherwise. Data persists. Contexts shift. Yesterday's normal becomes tomorrow's liability.
Privacy as Human Right vs. Privacy as Practical Necessity
I want to be honest with you. I care about privacy for two different reasons, and they do not always line up neatly. One is principled. One is practical. Both matter.
The human right argument says privacy is fundamental to human dignity. This is not my invention. Article 12 of the Universal Declaration of Human Rights explicitly protects against "arbitrary interference with his privacy, family, home or correspondence." The European Union enshrines privacy as a fundamental right in its Charter of Fundamental Rights. The reasoning is straightforward. Humans need private space to form thoughts, maintain relationships, and develop identity. Constant surveillance stunts human growth. It creates conformity. It kills dissent before it can form.
The practical argument works differently. It says privacy protects you from specific, measurable harms whether or not you believe in rights. Identity theft cost Americans $43 billion in 2023. Employment discrimination based on social media screening is widespread and often illegal but hard to prove. Insurance companies already use data brokers to adjust premiums. Landlords buy tenant screening reports that include information no human should use for housing decisions. These are not future risks. They are happening now.
I use both arguments because different people need different entry points. Some readers will care about dignity, autonomy, and the kind of society we are building. Others will care about their bank account, their job prospects, and their family's safety. Both are valid. Both lead to the same conclusion. Privacy matters. The mechanisms that strip it from us are harmful. We need tools and practices to reclaim it.
What You Will Learn in This Guide
If you have read this far, you probably have questions. Good. This guide exists to answer them with specificity and honesty. Here is what lies ahead.
We will map the surveillance landscape: who collects your data, how they do it, and what they do with it. We will build a framework for assessing your specific threat model and prioritizing accordingly. We will cover immediate actions, quick wins that cost nothing and significantly reduce exposure. We will build sustainable privacy practices and explore advanced tools and techniques for those who want to go further.
I will not promise that following this guide will make you invisible. Total privacy in the modern world is nearly impossible without extreme sacrifice. What I will promise is practical improvement. You will understand the systems that surveil you. You will have specific tools to resist them. You will be harder to track, harder to profile, and harder to exploit.
That is worth something. For Rebecca, Matthew, Ahmed, and countless others, it might have changed everything.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 2: What Is Privacy Really?


The Birth of a Legal Concept: Warren and Brandeis (1890)
Privacy as a legal concept did not exist until the late 19th century. Before 1890, American law recognized trespass, libel, and breach of confidence--but nothing specifically called "privacy." That changed with a landmark Harvard Law Review article that would reshape American jurisprudence.
In December 1890, Samuel Warren and Louis Brandeis published "The Right to Privacy" in the Harvard Law Review. The article, which has become the most cited law review piece in American legal history, was written in response to specific circumstances that still resonate today. Warren, a prominent Boston attorney, was incensed by the Boston newspapers' coverage of his daughter's wedding. The press had printed intrusive details about the private celebration, and Warren sought a legal remedy that did not exist at the time.
Brandeis and Warren argued that common law had evolved to protect not just property and contract rights, but also what they termed "the right to be let alone." They traced this right through earlier cases involving breach of confidence and implied contracts, constructing a legal theory that recognized an individual's interest in controlling the dissemination of personal information.
Prosser's Four Torts (1960)
William Prosser's 1960 California Law Review article, "Privacy," transformed Warren and Brandeis's philosophical concept into a practical legal framework. Where Warren and Brandeis had proposed a single, unified right, Prosser identified four distinct torts, each protecting different interests.
- Intrusion Upon Seclusion protects against intentional interference with solitude or private affairs.
- Appropriation of Name or Likeness prohibits using someone's identity for commercial purposes without consent.
- Public Disclosure of Private Facts prohibits the widespread dissemination of truthful but embarrassing private information.
- False Light protects against publicity that places a person in a false light that would be highly offensive to a reasonable person.
The Four Dimensions of Privacy
Beyond legal categories, privacy operates across four distinct dimensions that shape how individuals experience and protect their personal boundaries in daily life.
Physical Privacy
Control over your body, personal space, and physical environment. Protection against surveillance in private spaces and unwanted physical contact.
Informational Privacy
Control over personal data, records, and information. The right to know what's collected and how it's used.
Decisional Privacy
Autonomy over fundamental life choices. Freedom from interference in personal, medical, and family decisions.
Proprietary Privacy
Property interests in personal identity and data. Economic rights over how your information is monetized.
Privacy vs. Secrecy vs. Anonymity
These three terms are often conflated, but they describe distinct concepts with different legal and social implications.
Privacy is about control over information and access. A person can maintain privacy without secrecy by controlling who knows what and under what circumstances. Privacy operates on a spectrum of contexts and relationships rather than binary secrecy.
Secrecy is about concealment--keeping information hidden from everyone. Where privacy is relational (different people know different things), secrecy is absolute (nobody knows).
Anonymity is about identity separation--conducting activities without linking them to one's real-world identity. A person can be private without being anonymous (using real names but controlling information dissemination) or anonymous without being private (revealing extensive personal details under a pseudonym).
The Privacy Paradox


Study after study shows that people claim to value privacy highly. The 2019 Pew Research Center survey found that 81% of Americans feel they have little control over the data companies collect, and 79% are concerned about how companies use their data. Yet these same people routinely disclose personal information in exchange for minor conveniences, accept lengthy terms of service without reading them, and maintain social media profiles full of personal details.
This disconnect--between stated privacy preferences and actual behavior--is called the privacy paradox. Understanding it is essential for anyone designing privacy policies, building privacy-respecting products, or simply trying to protect their own information.
Several factors explain the paradox: Cognitive load is significant. Reading privacy policies would take an estimated 244 hours per year for the average internet user. Present bias plays a major role: privacy risks are delayed and probabilistic, while protections create immediate friction. Information asymmetry compounds the problem: users cannot meaningfully evaluate privacy risks because they lack information about data practices.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 3: The Digital Surveillance Economy


There's a parallel economy running beneath your daily life. You don't see it. You don't hear it. But it's been watching you for years. While you sleep, while you shop, while you scroll through your phone at 2 AM wondering why you can't fall asleep--someone is taking notes.
The Giants in the Shadows
Acxiom claims to have data on 2.5 billion people. Let that sink in. That's nearly every adult on Earth with a bank account, a phone, or a pulse. This Little Rock, Arkansas company--founded in 1969 when computers filled entire rooms--now maintains an estimated 1,500 data points on roughly 700 million consumers in the United States alone. Their clients include 47 of the Fortune 100 companies.
Experian made $6.6 billion in revenue in 2024. You probably know them from credit scores. That three-digit number that determines whether you can buy a house or lease a car. But Experian is far more than credit reports. They're one of the largest data brokers on the planet.
LexisNexis Risk Solutions generated over $2.5 billion in 2023. They sell what they call "identity intelligence" to law enforcement agencies, insurance companies, landlords, and employers.
CoreLogic specializes in property data--over 900 million property records covering 99.9% of U.S. properties. They know when you bought your house, how much you paid, what you owe on your mortgage, your property tax assessments, and even aerial imagery of your roof.
The 700 Data Points They Have on You
In 2014, the Federal Trade Commission conducted a study of nine major data brokers. The findings were staggering. These companies collect and sell data on nearly every American consumer, often organizing people into categories with names that sound like rejected reality TV shows.
"Rural Everlasting." That's code for older, low-income married couples in rural areas. "Apple Pie Families." Suburban middle-class families with children. "Zero Mobility." Low-income urban singles who rarely travel. The name alone is an insult wrapped in a data point.
But the categories are just the surface. The real treasure is in the individual data points--hundreds, sometimes thousands, of facts about your life:
- Your name, address, phone number, email addresses, and Social Security number
- Your date of birth, gender, marital status, education level, and occupation
- Your estimated income, net worth, credit score range, and how much debt you carry
- What kind of car you drive, how old it is, whether you lease or own it
- Your home's square footage, market value, the year it was built, and whether you have a pool
- Your political party registration, whether you vote in primary elections, and which causes you've donated to
- Your health conditions--or at least their best guess based on your purchases
- Your hobbies, travel patterns, and consumption preferences
How They Get It: The Harvesting Machine
Loyalty Programs: The Trojan Horse


Your CVS ExtraCare card saves you $3 on shampoo. In exchange, CVS gets a complete record of everything you buy: the medications, the personal care products, the occasional pregnancy test. CVS knows your health better than some doctors.
Credit Cards: The Spending Diary
Your credit card company knows everything you buy. Every restaurant, every gas station, every online purchase, every medical bill. Visa and Mastercard don't just process payments. They sell aggregated spending data to merchants, advertisers, and data brokers.
Public Records: The Government as Data Source
Every time you interact with the government, data brokers are watching. Property records, marriage and divorce records, court records, professional licenses, voter registration records--all scraped and sold.
Web Tracking: The Invisible Net
Every website you visit is probably tracking you. Cookies, pixel tags, fingerprinting scripts--they're everywhere. Facebook's "Like" button on a news article? It tracks you even if you don't click it. Google's advertising network appears on 75% of the top million websites.
The Target Story


In February 2012, a man walked into a Target store in Minneapolis and demanded to see the manager. He was angry. He was holding coupons. Coupons for cribs and baby clothes and diapers, addressed to his teenage daughter.
"Are you trying to encourage her to get pregnant?" he demanded.
The manager apologized, confused. A few days later, the man called back to apologize himself. His daughter was indeed pregnant. Target knew before he did.
Target's statisticians had analyzed purchase patterns of women who had signed up for baby registries. They found correlations: pregnant women bought unscented lotion around their second trimester, certain supplements, cotton balls and washcloths in specific combinations. Twenty-five products, analyzed together, could assign a "pregnancy prediction" score to any female shopper--and estimate due dates within a narrow window.
This wasn't an isolated case. It's the entire business model. Every data broker is trying to predict your behavior before you know it yourself.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 4: Corporate Data Harvesting


We talk about "Big Tech" like it's some abstract concept. It's not. It's five companies with a combined market cap that exceeds the GDP of most nations, and they know more about your daily life than your closest friends.
Google: The Archive of Human Intent


Every search query you've typed since 2005. Every YouTube video you've watched, including the ones you cleared from your history. Every location you've visited with an Android phone in your pocket. Google has it.
Search History: Google processes over 8.5 billion searches per day. Each one is stored, categorized, and analyzed. That late-night search for "signs of anxiety"? Saved. The medication you looked up? Associated with your profile.
Gmail: In 2017, Google announced it would stop scanning Gmail content for ad personalization. But Google didn't stop analyzing emails. They simply stopped using that analysis to show you ads directly. The scanning continues for other purposes.
Location Tracking: Google Maps Timeline reconstructs your movements with alarming precision--down to the minute you arrived at a restaurant, how long you stayed, and which route you took home. The company settled a lawsuit in 2022 for $391.5 million after continuing to track users who had explicitly disabled location tracking.
Meta: The Social Graph of Everything


Shadow Profiles: They maintain profiles on people who have never created Facebook accounts. Your friends uploaded their contact lists. Someone tagged you in a photo. A website with a Facebook pixel recorded your visit. Meta's algorithms stitched these fragments together--building a profile of a person who never consented to any of it.
Off-Facebook Activity: Meta's "Off-Facebook Activity" tool, launched in 2020, finally offered users a glimpse of this tracking. The typical report is overwhelming. Hundreds of apps. Thousands of data points. Your dating app activity. Your period tracker. Your religious app. All sharing data with Meta.
Emotion Manipulation: In 2014, Facebook published a research paper describing an experiment conducted on 689,003 users without their knowledge or consent. For one week, Facebook manipulated users' News Feeds. The study proved that Facebook could manipulate users' emotions at scale.
Amazon: The Commerce Panopticon
Purchase History: Every item you've bought. Every item you almost bought--saved in abandoned carts. Every item you searched for. Amazon tracks 2,000+ data points per user interaction.


Alexa: Amazon sold over 500 million Alexa-enabled devices. These devices record audio when they detect the wake word--and sometimes when they think they detect it. Amazon employs thousands of workers to listen to and transcribe these recordings. In 2023, Amazon agreed to pay $31 million in fines after the FTC found that Ring had allowed employees unrestricted access to customer videos.
Apple: Privacy Theater vs. Privacy Reality
Apple collects your name, address, email, phone number, and payment information. They store your App Store purchase history, iCloud documents, and device backups. When you use Siri, your voice recordings may be sent to Apple servers.
iCloud: iCloud backups are encrypted, but Apple holds the encryption keys. This means Apple can access your iCloud data and can provide it to law enforcement with a warrant. In 2021, Reuters reported that Apple had abandoned plans to offer end-to-end encryption for iCloud backups after the FBI objected.
App Tracking Transparency: Apple's 2021 introduction of ATT was genuinely significant. But ATT doesn't prevent tracking within Apple's ecosystem. Apple's own advertising revenue tripled to $7 billion annually after ATT was implemented, largely at competitors' expense.
Technical Mechanisms: The Invisible Infrastructure
- Browser Fingerprinting: Your browser leaks information--screen resolution, installed fonts, time zone, browser plugins--creating a fingerprint unique enough to identify you with 99% accuracy, even with cookies disabled.
- Canvas Tracking: Websites can use the HTML5 canvas element to fingerprint your device based on how your graphics card handles rendering.
- Ultrasonic Beacons: Some apps emit high-frequency sounds above human hearing to track your location across physical spaces.
- CNAME Cloaking: Advertisers set cookies that appear to come from the site you're visiting while actually being controlled by a tracking company.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 5: Government Surveillance


In June 2013, a 29-year-old contractor named Edward Snowden boarded a flight to Moscow with four laptops containing classified documents that would forever change how the world understood government surveillance.
The Snowden Revelations: What We Learned


PRISM: A program allowing the National Security Agency to collect communications directly from the servers of nine major technology companies: Microsoft (2007), Yahoo (2008), Google and Facebook (2009), YouTube (2010), Skype and AOL (2011), and Apple (2012).
XKeyscore: Allows analysts to search "virtually everything" an individual does on the Internet. A single query could retrieve email content, browsing history, social media activity, and metadata. The system processed approximately 41 billion records per day as of 2008.
Bulk Telephone Metadata: Verizon was ordered to provide the NSA with "all call detail records" including originating and terminating phone numbers, IMSI numbers, IMEI numbers, and the time and duration of calls.
The Eyes Have It: Global Intelligence Alliances
Five Eyes represents the most comprehensive alliance, formalized through the UKUSA Agreement of 1946. The member nations--the United States, United Kingdom, Canada, Australia, and New Zealand--maintain integrated signals intelligence operations.
Nine Eyes expands this circle to include Denmark, France, the Netherlands, and Norway. Fourteen Eyes adds Belgium, Germany, Italy, Spain, and Sweden.
These alliances matter because they enable circumvention of domestic surveillance restrictions. When NSA analysts were prohibited from targeting U.S. persons directly, they could request that GCHQ conduct the surveillance and share the results.
Global Surveillance Systems
China's Social Credit System draws data from an estimated 626 million CCTV cameras, mobile device location tracking, payment records, internet browsing monitored through the Great Firewall, and behavioral data from smart city sensors.
Russia's SORM requires telecommunications providers to install FSB-provided equipment enabling real-time interception of all communications without provider knowledge of specific targets. SORM-3 requires providers to store all communications metadata for three years and content for six months.
The United Kingdom's Investigatory Powers Act 2016 creates a comprehensive framework: internet connection records must be retained for 12 months; bulk interception warrants can be issued by the Secretary of State.
Facial Recognition: The Biometric Revolution


Clearview AI built a database of over 50 billion facial images scraped from public websites without consent. By 2023, Clearview AI reported over 3,100 law enforcement agency customers across 32 countries.
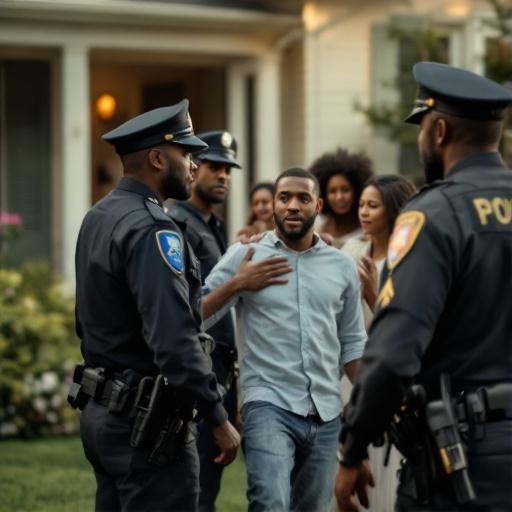
Accuracy remains contested. The NIST Face Recognition Vendor Test 2019 found that false positive rates were 10 to 100 times higher for African American and Asian faces compared to Caucasian faces in many algorithms. The Robert Williams case in Detroit (January 2020) demonstrated these failures: Williams was arrested on his front lawn after facial recognition software incorrectly matched him to shoplifting surveillance footage.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 6: Privacy in the Age of AI


Machine learning has transformed the privacy landscape in ways that were difficult to anticipate even a decade ago. The systems we've built can find patterns in billions of data points, generate convincing human-like content, and make predictions about individual behavior.
Training Data: The Consent Crisis


Every large language model, image generator, and recommendation system depends on training data--massive collections of text, images, audio, and behavioral logs. GPT-4, Claude, and similar models were trained on hundreds of billions of words scraped from the internet. Image models like DALL-E 3, Midjourney, and Stable Diffusion learned from billions of images, many scraped from photo-sharing sites, artist portfolios, and personal blogs.
The consent problem emerges from how this data was collected. Much of it came from public sources, but "public" does not mean "intended for AI training." A person posting on a forum in 2005, uploading a photo to Flickr in 2010, or writing a blog post in 2015 likely never imagined their content would be used to train systems that could generate similar content.
Training datasets have been found to contain personal emails, medical records, phone numbers, and home addresses. In 2021, researchers discovered that GPT-2 could generate working email addresses and phone numbers that appeared in its training data.
Inference Attacks: Extracting Secrets from Models
Membership inference attacks allow an attacker to determine whether a specific individual's data was included in the training set by observing how the model responds to certain inputs.
Model inversion attacks attempt to reconstruct actual training examples from model outputs. In 2015, researchers showed they could recover recognizable images of people's faces from facial recognition models.
Extraction attacks targeting large language models demonstrated that researchers could extract verbatim text from GPT-2 by prompting it with specific prefixes--including personally identifiable information.
Facial Recognition: The End of Anonymity in Public Spaces
Clearview AI built its database by scraping billions of photos from social media platforms without users' knowledge or consent. The company claims its database contains over 30 billion images. A stranger who photographs you at a protest, a bar, or a medical clinic could potentially identify you, find your social media profiles, and learn where you work and live.
Voice Cloning: Three Seconds Is Enough


Modern voice cloning systems can generate convincing replicas of a person's voice from remarkably small samples--sometimes as little as three seconds of audio. In 2019, criminals used voice cloning to impersonate a CEO's voice in a $243,000 fraud scheme.
Behavioral Prediction: When AI Anticipates Your Actions
Machine learning systems excel at prediction. Target's pregnancy prediction algorithm could identify pregnant customers based on subtle changes in purchasing patterns--switching to unscented lotion, buying cotton balls, purchasing certain supplements. The system assigned customers a "pregnancy prediction" score and targeted them with relevant coupons.
Modern systems integrate data from multiple sources--purchase history, browsing behavior, location data, social media activity, credit reports--to build comprehensive models of individual behavior. Health insurers use predictive models to identify customers who may develop expensive conditions. Employers use algorithms to predict which workers are likely to quit. Law enforcement agencies use "predictive policing" systems to forecast where crimes will occur.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 7: The Internet of Things


I remember the first time I unboxed an Amazon Echo. There was something almost magical about saying "Alexa, play some jazz" and having music fill the room. What I didn't spend that hour doing? Reading the 15,000-word privacy policy that essentially gave Amazon permission to record everything within earshot.
The Always-On Roommates: Smart Speakers
Amazon has sold over 500 million Alexa-enabled devices. Google has shipped more than 100 million Google Home units. These devices sit on our kitchen counters, nightstands, and coffee tables--permanent fixtures in our most private spaces.
Smart speakers use "wake word" detection to listen for their activation phrase. But to detect "Alexa" or "Hey Google," the microphone must be actively processing everything it hears. The device isn't recording and transmitting constantly--technically. Instead, it's in a state of perpetual listening, analyzing sound waves for patterns that match the wake word.


In 2018, a woman in Portland discovered her Echo had recorded a private conversation and sent it to one of her husband's employees. Amazon employs thousands of contractors to listen to Alexa recordings--ostensibly to improve accuracy. These workers have access to audio clips containing intimate conversations, arguments, sexual encounters, and criminal activity.
The Screen That Watches Back: Smart TVs


Modern televisions are computers with displays attached. They run operating systems, connect to WiFi, download apps, and--critically--collect data about everything you watch. This is called Automatic Content Recognition (ACR), and it's standard on virtually every smart TV sold today.
Your TV captures pixels from the screen and compares them against a database of known content. This happens regardless of input source. The data collected is far more granular than most users realize. Your TV knows what you watch, when you watch it, how long you watch it, and when you change the channel.
Vizio made headlines in 2017 when the FTC fined the company $2.2 million for tracking viewing habits without proper consent from 11 million televisions since 2014.
Quantified Selves: Fitness Trackers and Health Data
Apple has sold over 100 million Apple Watches. Fitbit (now owned by Google) has sold more than 120 million devices. This data is intimate in ways we rarely consider. Your heart rate variability can indicate anxiety, depression, or cardiovascular issues. Your sleep patterns reveal work stress, relationship problems, or substance use.

In 2018, Strava published a "heat map" showing aggregated user activity around the world. The map also revealed the locations of secret military bases in Afghanistan, Syria, and Somalia. Soldiers wearing fitness trackers had inadvertently mapped sensitive installations simply by jogging around their compounds.
Connected Cars: Four-Wheel Surveillance


Modern vehicles are computers on wheels, generating and transmitting vast quantities of data. A typical new car contains 100+ microprocessors, multiple cellular connections, and increasingly sophisticated sensors tracking everything from engine performance to driver behavior.
The data generated is staggering: location history, speed patterns, acceleration and braking behavior, seatbelt usage, infotainment preferences, phone contacts synced via Bluetooth, voice commands, even biometric data from steering wheel sensors.
The 2023 Mozilla Foundation study of car privacy ranked automotive as the worst product category for privacy. Every major manufacturer received failing grades.
The Mirai Botnet: When IoT Attacks


In October 2016, a massive DDoS attack took down major internet services including Twitter, Netflix, Reddit, and CNN. The attack traffic--reaching 1.2 terabits per second--came from compromised security cameras, DVRs, and baby monitors. At its peak, Mirai controlled over 600,000 devices.
Most IoT devices have terrible security: default passwords that can't be changed, unencrypted communications, no automatic update mechanisms. When your insecure baby monitor becomes part of a botnet attacking hospitals, your device has become a public health hazard.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 8: Social Media Oversharing


We all know the feeling. The vacation photo that absolutely must be posted. The witty observation that demands an audience. The moment of vulnerability that somehow migrates from private thought to public post. The question isn't whether this happens--it's why, despite knowing better, we keep doing it.
The Broadcast Impulse: Why We Share
In 2012, researchers at Harvard University conducted fMRI studies showing that self-disclosure activates the same neural pathways as primary rewards like food and money. Participants were willing to forgo money for the opportunity to share information about themselves.
Social media platforms didn't simply stumble upon this neurological quirk. They engineered for it. The variable reward schedule--will this post get 10 likes or 1,000?--is borrowed directly from slot machine psychology.
Sharenting: The Consent We Never Asked For
Before a child can walk, their digital dossier already exists. A 2019 study by Nominet found that by age five, the average child has 1,500 photos of them posted online. By age 13, when most social media platforms allow children to create their own accounts, their parents have already constructed a digital identity for them.
Children's photos are regularly scraped from social media and repurposed in ways parents never anticipate. A 2023 investigation by the Australian eSafety Commissioner found that 50% of material in some child exploitation forums originated from innocent family photos shared publicly on social media.
Digital Footprints That Never Disappear
Platforms offer delete buttons, and we treat them like they work. Click "Delete," watch the post disappear from your timeline, and assume it's gone. This assumption is dangerously wrong.
When you delete a social media post, you're typically only removing the public-facing reference. The underlying data--stored in databases, backed up to disaster recovery systems, logged in analytics pipelines--often remains intact. Screenshots represent another permanence vector that no deletion policy can address.
Employment Screening: The Resume You Never Submitted


Seventy percent of employers check social media during hiring processes. Companies like Fama and Checkr offer AI-powered social media background checks that scan candidates' accounts for "toxic behavior" or content that might "damage brand reputation."


In 2017, Harvard College rescinded admissions offers to at least ten incoming freshmen after discovering they had shared offensive memes in a private Facebook group. The students had considered the group private and anonymous; Harvard's admissions office considered it relevant to character assessment.
Insurance and Social Media: Claims Denied Based on Posts


Insurance companies have been monitoring claimants' social media for over a decade. In 2011, a Quebec woman had her disability benefits terminated after her insurance company discovered Facebook photos showing her at a bar and on vacation. The woman suffered from depression; her insurer argued that social activity demonstrated she was not disabled.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 9: Identity Theft & Financial Privacy


In 2020, identity theft touched nearly 49 million Americans--roughly one in every seven adults in the United States. The financial damage was staggering: $56 billion in losses.
The Scale of the Problem
By 2023, the Identity Theft Resource Center reported that publicly reported data breaches had set a new record, exposing hundreds of millions of records. Identity theft rarely announces itself with a single catastrophic event. More commonly, it begins with a small charge on a credit card statement, a denied loan application, or a collections notice for an account the victim never opened.
How It Happens: The Theft Playbook
Data Breaches
When hackers penetrate company defenses, they obtain Social Security numbers, dates of birth, addresses, and financial account details sold on dark web marketplaces. The 2017 Equifax breach exposed 147 million Americans.
Phishing
Modern phishing campaigns use sophisticated techniques: emails that perfectly mimic bank communications, text messages claiming package delivery issues, phone calls from "IRS agents." In 2023, phishing schemes resulted in $2.9 billion in losses.
SIM Swapping
Criminals convince mobile carrier employees to transfer your phone number to a device they control. Once they control the phone number, they can intercept two-factor authentication codes and drain accounts.
Credential Stuffing
Attackers use username-password combinations from data breaches to attempt logins across thousands of websites. If you reused passwords, a breach at one site becomes a breach everywhere.
Financial Privacy Tools: Practical Defenses
Credit Freezes: A credit freeze prevents creditors from accessing your credit report. Without access, most lenders won't open new accounts. Federal law mandates free credit freezes from Equifax, Experian, and TransUnion.
Fraud Alerts: When you place a fraud alert, creditors must take extra steps to verify your identity before opening new accounts. Initial fraud alerts last one year and can be renewed.
Virtual Cards: Virtual credit cards generate temporary, single-use or merchant-specific card numbers linked to your actual account. If a virtual card number is compromised, it's useless elsewhere.
Cryptocurrency and Privacy: The Transparency Paradox
A persistent myth suggests that cryptocurrency transactions are anonymous. They are not. Bitcoin and most major cryptocurrencies operate on public blockchains--permanent, transparent ledgers recording every transaction. While wallet addresses don't directly reveal identities, the combination of transaction patterns, exchange records, and blockchain analysis often deanonymizes users.
Privacy coins like Monero, Zcash, and Dash attempt to solve this through cryptographic techniques that obscure transaction details. However, several major exchanges have delisted privacy coins due to concerns about money laundering.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 10: Privacy Tools & Practical Defense


You've made it this far. You understand the surveillance economy. Now comes the part everyone asks: What do I actually do about it? This section isn't about achieving perfect privacy--that's a fantasy. It's about making surveillance harder, more expensive, and less comprehensive.
Browser Privacy: Your Gateway to the Web
Firefox
The only major browser not controlled by an advertising company. Enhanced Tracking Protection blocks known trackers by default. Container tabs isolate cookies between sites.
Setup: Set Enhanced Tracking Protection to "Strict." Change default search engine to DuckDuckGo. Install uBlock Origin.
Brave
A Chromium-based browser that strips out Google's tracking and adds built-in privacy protections. Blocks ads and trackers natively, making pages load faster.
Caveat: The cryptocurrency integration (BAT) and history of adding referral codes to URLs has created trust issues.
Tor Browser
Routes traffic through three volunteer-run relays, encrypting at each hop. Your IP address is hidden from the websites you visit.
Use for: Whistleblowing, researching sensitive topics, bypassing censorship. Expect 3-10x slower speeds.
VPNs: What They Actually Do
A VPN creates an encrypted tunnel between your device and a VPN server. Your ISP can see that you're using a VPN but can't see which websites you visit. The websites see the VPN server's IP address, not yours.
VPNs Help When:
- You're on public WiFi and want to prevent local network snooping
- Your ISP blocks certain sites or throttles specific traffic
- You want to appear to be in a different country
VPNs Don't Help When:
- You're logged into Google/Facebook/Amazon--they still know who you are
- You're trying to hide from law enforcement with a warrant
- You want to prevent browser fingerprinting
Recommended providers: Mullvad (anonymous account numbers, accepts cash), IVPN (transparent ownership, regular audits), Proton VPN (Swiss jurisdiction, open source).
Password Managers: The Foundation of Account Security
If you're using the same password on more than one site, you're one data breach away from losing multiple accounts. Password managers solve this by generating and storing unique, random passwords for every service.
Bitwarden (Recommended): Open source, regularly audited, free tier covers most needs, works on everything.
1Password: Polished interface, Travel mode removes sensitive vaults when crossing borders. $36/year.
KeePassXC: Completely offline, local database you control completely. Steep learning curve.
Two-Factor Authentication: The Second Line of Defense
SMS 2FA: Better than nothing, but vulnerable to SIM swapping and SS7 protocol attacks.
TOTP (Time-Based One-Time Password): Apps like Authy or Aegis generate 6-digit codes that change every 30 seconds. Works offline, codes aren't transmitted.
Hardware Security Keys: Physical devices like YubiKeys implement phishing-resistant authentication. The key cryptographically proves it belongs to the legitimate site.
Encrypted Messaging: Beyond WhatsApp
Signal: The gold standard. Open source, funded by a nonprofit, designed by cryptographers. End-to-end encryption by default, sealed sender, minimal metadata collection.
Session: No phone number required. Uses onion routing similar to Tor.
Email Privacy
ProtonMail and Tutanota: Both offer end-to-end encryption when emailing other users of the same service. Swiss and German jurisdiction respectively.
Email Forwarding (SimpleLogin, AnonAddy): Create unlimited aliases that forward to your real inbox. When a service leaks your email, you know who did it.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 11: Health & Medical Privacy


You'd never post your medical records on social media. Yet every day, companies you've never heard of are buying, selling, and trading details about your prescriptions, your DNA, your mental health struggles, and your fertility patterns.
The HIPAA Mirage: What Actually Gets Protected
Most Americans believe HIPAA creates an impenetrable shield around their medical information. This belief is dangerously wrong. HIPAA applies only to specific entities called "covered entities": healthcare providers, health plans, and healthcare clearinghouses. If your doctor's office shares your records with another hospital, HIPAA applies. If that same information winds up in the hands of a data broker, it often doesn't.
What HIPAA explicitly doesn't cover: Fitness trackers, health apps not offered by healthcare providers, genetic testing companies (unless processing tests ordered by your doctor), and wellness programs offered directly by employers.
Mental Health Apps: Therapy at What Cost?
BetterHelp, owned by Teladoc Health, became the poster child for mental health data exploitation. In 2023, the FTC reached a settlement following revelations that the company had shared sensitive mental health information with Facebook, Snapchat, and other advertising platforms--including answers to intake questionnaires about suicidal thoughts or hospitalizations. The company paid $7.8 million to settle.
Similar issues emerged with Monument and Tempest, two addiction recovery apps that used Meta's advertising pixel to share information about users' alcohol consumption patterns and recovery progress with Facebook.
Period Trackers and the Post-Dobbs Privacy Crisis
The Supreme Court's 2022 decision in Dobbs v. Jackson Women's Health Organization transformed period tracking apps from wellness tools into potential evidence sources. Investigations revealed that popular apps including Flo, Clue, and Ovia shared data with dozens of third parties.
The data these apps collect is extraordinarily sensitive: menstrual dates, sexual activity, pregnancy test results, symptoms of miscarriage, attempts to conceive. In a post-Dobbs landscape, this information could potentially identify individuals seeking or obtaining abortions.
Genetic Testing: The DNA You Can't Change
If credit card numbers and email addresses are the currency of routine identity theft, DNA is the crown jewel of biometric data. You can cancel a credit card. You can't change your genetic code.
23andMe's October 2023 data breach exposed the genetic and ancestry data of approximately 6.9 million users. Genetic data is inherently identifying: it connects you to your relatives, reveals your disease risks, and can potentially predict your physical characteristics. When 23andMe loses your DNA data, they lose something you share with your children, your parents, and your siblings--whether those relatives consented to testing or not.
Wearables and Wellness Programs
Employer wellness programs represent a particularly thorny data sharing vector. Under the Affordable Care Act, employers can offer significant incentives--up to 30% of health insurance premiums--for participation. These programs often require sharing fitness tracker data, completing health risk assessments, or meeting biometric targets.
Insurance companies increasingly demand access to wearable data in exchange for premium discounts. If your tracker shows irregular heart rhythms, does your insurer know? If your sleep quality suggests depression, could that affect your coverage?


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 12: Workplace Privacy


Your employer is watching you work. Not metaphorically. Actually watching. Recording. Logging every keystroke, screenshot, and bathroom break. The modern workplace has become a panopticon of granular surveillance, and most employees have no idea how deep the monitoring goes.
The Employee Surveillance Toolkit
ActivTrak captures screenshots every time an employee clicks, tracks application usage down to the second, and assigns "productivity scores." It records every website visit, every file opened, every window title changed.
Teramind uses keystroke logging to capture every character typed, including deleted text. It records all emails, instant messages, and file transfers. It can silently turn on webcams and microphones.
Hubstaff combines time tracking with screenshot capture (every 10 minutes by default), application monitoring, and GPS tracking for mobile workers.
The pricing reveals how ubiquitous this has become. ActivTrak starts at $10 per user per month. These aren't tools reserved for high-security environments--they're affordable enough that a 20-person company can monitor every employee for less than the cost of a single catered lunch.
Reading Your Messages: Email and Slack Surveillance
Every corporate communication platform you've used--Outlook, Gmail for Business, Slack, Microsoft Teams, Zoom chat--comes with administrative capabilities that most employees never see. Your "private" messages aren't private. Your "direct" messages aren't direct. Everything is archived, searchable, and accessible to employers with the right access levels.
Slack's Enterprise Grid and Business+ plans include "compliance exports"--complete archives of all messages, including those from private channels and direct messages. These exports capture not just text but file uploads, emoji reactions, and edit histories.
BYOD: When Your Phone Becomes Company Property
Mobile Device Management (MDM) software like Microsoft Intune gives employers administrative control over personal devices. These platforms can enforce password policies, restrict app installations, remotely wipe devices, and access location data. When you install a work email profile on your phone, you're likely installing an MDM certificate that grants these capabilities.
Remote Work Surveillance
The shift to remote work intensified surveillance. Screenshot capture became the default mode. Some platforms take webcam photos of employees every few minutes throughout the workday. Mouse and keyboard tracking provides the foundation for "activity levels" that determine pay and employment.
Union Busting and Surveillance
The most aggressive workplace surveillance targets workers attempting to organize. Amazon maintains a Global Security Operations Center that monitors workers across facilities. During union drives, Amazon deployed algorithms tracking employee sentiment, analytics tools identifying "hotspots" of organizing activity, private investigators to infiltrate break rooms, and social media monitoring for pro-union content.
The National Labor Relations Board found that Amazon illegally surveilled and threatened workers during the Bessemer union drive, but the company faced no meaningful penalties.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 13: Children's Privacy


Before a child takes their first steps, before they can form memories, their digital identity already exists. A 2020 study found that the average child has 1,500 photos of them posted online before their fifth birthday--roughly one photo every day of their life.
The First Digital Footprint


This is the reality of "sharenting," the practice of parents sharing information about their children on social media. By age thirteen, when most platforms allow children to create their own accounts, their parents have already constructed a digital identity for them--one they had no role in shaping and cannot control.
Children's photos are routinely scraped by facial recognition databases. A 2019 study by NYU researchers found that photos of children posted publicly were being used to train machine learning models without any safeguards.
COPPA: Toothless Legislation in a Digital Playground
The Children's Online Privacy Protection Act requires verifiable parental consent before collecting personal data from children under thirteen. In practice, COPPA is a study in regulatory failure. The FTC has issued only 34 COPPA enforcement actions in over two decades. YouTube's 2019 COPPA settlement--$170 million--represents approximately two days of the platform's ad revenue.
The law is riddled with loopholes. The "actual knowledge" loophole allows platforms to claim they didn't "know" a user was under thirteen. The "school consent loophole" allows educational technology providers to bypass parental consent entirely if a school contracts with them.
EdTech: The Classroom as Data Collection Zone
Chromebooks account for over 60% of devices in U.S. K-12 schools. Google Workspace for Education is used by over 150 million students and educators worldwide. When a child opens a Chromebook, they're logged into a Google ecosystem that tracks search history, browsing activity, documents created, location data, YouTube viewing history, and third-party app usage.
Google's privacy policy for education services promises not to use student data for advertising. What it doesn't promise is to delete that data. A student's entire educational digital footprint can be retained indefinitely.
Location Tracking: When Parental Monitoring Becomes Surveillance
Life360 has over 33 million active users, predominantly families tracking children. The app provides real-time location, driving speed monitoring, and "place alerts." Life360 was found selling location data to data brokers in 2021.
The normalization of constant tracking raises fundamental questions about child development. A teenager who knows their parent receives an alert if they leave school grounds, whose driving speed is monitored, whose location is visible at all times, develops under conditions of constant observation.
Future Implications: AI Training on Childhood Data
LAION-5B, a dataset used to train Stable Diffusion and other image generation models, contains billions of images scraped from the internet--including millions of photos of children. These photos, originally posted by parents, appear in the dataset with their original captions, locations, and sometimes identifying information.
Clearview AI has scraped billions of photos from social media, including extensive images of children. The company's database allows law enforcement to identify individuals from photos--including children who have no criminal record, no reason to be in a police database, yet whose faces are searchable because their parents posted photos online.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Section 14: Global Privacy Laws


When the European Union's General Data Protection Regulation took effect in May 2018, it didn't just change how companies handled data--it forced a global conversation about privacy rights that had been largely theoretical.
GDPR: The Original Shockwave
GDPR applies to any organization processing EU residents' data, regardless of where that organization is headquartered. Data subjects have the right to access their personal information, the right to request deletion ("right to be forgotten"), the right to data portability, and the right to object to automated decision-making.
GDPR allows penalties up to 20 million euros or 4% of global annual turnover. In 2023, Meta received a 1.2 billion euro fine for unlawful data transfers to the United States. Amazon paid 746 million euros in 2021. Google has accumulated multiple fines across Europe.
Yet privacy advocates increasingly question whether GDPR is actually working. The Irish Data Protection Commission, responsible for overseeing most major tech companies, has been criticized as a bottleneck. The Meta fine took four years of investigation.
CCPA and CPRA: California's Experiment
California's Consumer Privacy Act gave residents the right to know what personal information businesses collect about them, the right to delete that information, the right to opt-out of its sale, and the right to non-discrimination for exercising these rights.
The California Privacy Rights Act, effective 2023, added the right to correct inaccurate information, stricter requirements for handling sensitive personal data, and new obligations around automated decision-making. It created a dedicated enforcement agency--the California Privacy Protection Agency.
The Emerging State-by-State Maze
California started the trend, but other states have followed with their own variations:
- Virginia's CDPA (2021): More business-friendly. Requires consumers to opt-out rather than businesses obtaining opt-in consent.
- Colorado Privacy Act (2021): Requires universal opt-out mechanisms.
- Connecticut, Utah, and Beyond: At least 15 additional states passed comprehensive privacy laws by 2024.
For a company operating nationally, this means maintaining potentially 20+ different compliance programs, each with unique requirements.
The International Landscape
| Jurisdiction | Effective | Opt-In/Opt-Out | Max Fine |
|---|---|---|---|
| EU (GDPR) | 2018 | Opt-in for sensitive data | 20M euros or 4% revenue |
| California (CCPA/CPRA) | 2018/2023 | Opt-out for sale; opt-in for sensitive | $2,500-$7,500 per violation |
| Brazil (LGPD) | 2020 | Opt-in for sensitive data | 2% revenue, max R$50M |
| China (PIPL) | 2021 | Opt-in for sensitive data | 50M yuan or 5% revenue |
| Singapore (PDPA) | 2012/2020 | Opt-out for marketing | $1M SGD |
| Japan (APPI) | 2003/2020 | Opt-out for third-party sharing | ~$100K USD |
Why There's No Federal US Privacy Law
The United States remains an outlier among developed economies in lacking comprehensive federal privacy legislation. The reasons are structural: Republicans generally oppose federal preemption of state laws; Democrats typically want stronger protections than Republicans will support; the California delegation fights preemption clauses; and tech industry lobbying has successfully blocked legislation.
The American Data Privacy and Protection Act, introduced in 2022, came closer than previous attempts but stalled over disagreements about private right of action, preemption of state laws, and algorithmic decision-making protections.
The Enforcement Reality Gap
For all the headlines about billion-dollar fines, the enforcement picture is less impressive than it appears. The Irish Data Protection Commission had fewer than 200 staff as of 2024. It takes an average of 24-36 months to resolve major cases. Studies found that only 42% of data subject access requests to major companies received complete responses within the mandated timeframe.
The patchwork of global privacy laws represents an ongoing experiment in regulating data in a borderless digital economy. What remains clear is that privacy law will continue evolving--and the fundamental tension between data-driven business models and individual privacy rights will remain unresolved.


Interested in a Credit Privacy File registered with the IRS? Get legal standing in commerce that's completely separate from your SSN credit profile.
Download Your Free Guide
Frequently Asked Questions About Privacy Protection
What is digital privacy and why does it matter?
Digital privacy refers to your right to control what personal information is collected about you online, how it is used, and who can access it. It matters because data breaches, identity theft, and surveillance can lead to financial loss, reputation damage, employment discrimination, and loss of personal autonomy.
What is a credit privacy file?
A credit privacy file is a separate credit profile registered with the IRS that provides legal standing in commerce independent from your Social Security Number credit history. This allows individuals to establish a distinct financial identity for business and personal transactions.
How do data brokers collect my personal information?
Data brokers collect information from public records, social media, loyalty programs, credit card transactions, app usage, web tracking cookies, and purchased datasets. Companies like Acxiom maintain over 1,500 data points on 700 million U.S. consumers.
What is the difference between privacy and anonymity?
Privacy is about controlling who knows what about you and under what circumstances. Anonymity is about conducting activities without linking them to your real identity. You can be private without being anonymous, and anonymous without being private.
How can I protect myself from identity theft?
Protect yourself by using strong unique passwords, enabling two-factor authentication, freezing your credit with all three bureaus, monitoring your credit reports, being cautious with phishing attempts, using a VPN on public WiFi, and limiting personal information shared online.
What is GDPR and does it apply to me?
GDPR (General Data Protection Regulation) is the EU's privacy law that grants rights including data access, deletion, and portability. It applies to EU residents and any company serving EU customers, regardless of where that company is located.
What rights do I have under CCPA?
Under California's CCPA/CPRA, you have the right to know what data is collected, request deletion, opt out of data sales, correct inaccurate information, and limit use of sensitive data. These rights apply to California residents regardless of where the company is based.
How does Google track me?
Google tracks you through search queries, Gmail content, YouTube viewing history, location data from Android and Maps, Chrome browsing history, voice commands to Assistant, and advertising network cookies across 75% of top websites.
What is a VPN and should I use one?
A VPN (Virtual Private Network) encrypts your internet traffic and masks your IP address, protecting you from surveillance on public networks. You should use one when on public WiFi, accessing sensitive accounts, or when you want to prevent your ISP from tracking your browsing.
How do smart home devices compromise privacy?
Smart home devices like Alexa, Google Home, smart TVs, and Ring cameras continuously collect audio, video, and behavioral data. This data can be accessed by the manufacturer, shared with third parties, subpoenaed by law enforcement, or exposed in data breaches.
What is facial recognition and how is it used?
Facial recognition uses AI to identify individuals from images or video. It is used by law enforcement, retailers for loss prevention, airports for boarding, social media for tagging, and advertisers for targeted marketing. Clearview AI has scraped over 30 billion faces.
How can I opt out of data broker databases?
You can opt out by submitting removal requests to each data broker individually. Major brokers include Acxiom, Experian, LexisNexis, Spokeo, and WhitePages. Services like DeleteMe and Privacy Duck automate this process for a fee.
What information do social media platforms collect?
Social media platforms collect your posts, messages, photos, location data, device information, contacts, browsing history on partner sites, ad interactions, and biometric data like face geometry. Facebook maintains shadow profiles on non-users.
Is my health data protected by HIPAA?
HIPAA only protects health data held by covered entities like hospitals and insurers. Health apps, fitness trackers, DNA testing services, and period-tracking apps are generally not covered by HIPAA and can share your data freely.
Can my employer monitor my work computer?
Yes, employers can legally monitor company devices including emails, keystrokes, screen activity, file access, and web browsing. Many also use productivity tracking software. Remote work has increased surveillance with tools like Time Doctor and Hubstaff.
What privacy protections exist for children online?
COPPA requires parental consent before collecting data from children under 13. New state laws require age verification and design constraints for minors. However, enforcement is limited and many platforms collect children's data despite restrictions.
What is end-to-end encryption?
End-to-end encryption ensures only you and your intended recipient can read messages - not the platform, hackers, or government. Apps with E2E encryption include Signal, WhatsApp (for messages), and iMessage. It protects against interception.
How do credit bureaus collect my data?
Credit bureaus receive data from lenders, credit card companies, collection agencies, and public records. They track payment history, credit utilization, account ages, inquiries, and public records like bankruptcies. This data follows you throughout your life.
What is a credit freeze and how do I get one?
A credit freeze prevents new accounts from being opened in your name by blocking access to your credit report. It is free to place and lift at Equifax, Experian, and TransUnion. You should freeze your credit proactively, not just after a breach.
How does location tracking work on my phone?
Your phone tracks location via GPS, cell tower triangulation, WiFi network detection, and Bluetooth beacons. This data is accessed by apps, sold to data brokers, used for advertising, and can be subpoenaed by law enforcement.
What are cookies and tracking pixels?
Cookies are small files websites store on your device to track behavior. Tracking pixels are invisible images that report when emails are opened or pages viewed. Both enable cross-site tracking and targeted advertising profiles.
How can I make my browser more private?
Use Firefox or Brave instead of Chrome. Install uBlock Origin and Privacy Badger extensions. Enable strict tracking protection. Use a privacy-focused search engine like DuckDuckGo. Clear cookies regularly or use containers to isolate sessions.
What is the privacy paradox?
The privacy paradox describes how people claim to value privacy highly but routinely share personal information for minor conveniences. It is explained by cognitive load, present bias (immediate benefits vs future risks), and information asymmetry.
How do I request my data from a company?
Submit a data subject access request (DSAR) citing GDPR Article 15 or CCPA rights. Companies must respond within 30-45 days. You can request what data they have, how it is used, who it was shared with, and request deletion.
What is browser fingerprinting?
Browser fingerprinting identifies you without cookies by collecting unique combinations of browser settings, installed fonts, screen resolution, plugins, and hardware. It is harder to block than cookies and can track you across sessions.
Are password managers safe to use?
Yes, reputable password managers like 1Password, Bitwarden, and Dashlane are much safer than reusing passwords. They use strong encryption and enable unique complex passwords for every site. Use one with a strong master password and 2FA.
What is two-factor authentication and why use it?
Two-factor authentication (2FA) requires something you know (password) plus something you have (phone or key). It prevents account takeover even if your password is compromised. Use authenticator apps or hardware keys rather than SMS codes.
How do I know if my data was in a breach?
Check HaveIBeenPwned.com with your email addresses. Sign up for credit monitoring services. Enable breach alerts from your password manager. Major breaches are often reported in news. Assume your data has been exposed and act accordingly.
What privacy settings should I change on my phone?
Disable ad tracking (Limit Ad Tracking on iOS, Opt Out of Ads Personalization on Android). Review app permissions for location, camera, microphone. Disable personalized ads. Turn off WiFi and Bluetooth scanning. Limit lock screen notifications.
What is a credit privacy file registered with the IRS?
A credit privacy file registered with the IRS is a legitimate alternative financial identity that provides legal standing in commerce separate from your SSN credit profile. This allows you to conduct business and personal transactions with a distinct credit history. Download our free guide to learn more.
Ready to take control of your financial privacy? Get your Credit Privacy File registered with the IRS for legal standing in commerce.
Download Your Free Guide Now


